For users using the 3CX web client or desktop app, if the firewall on the 3CX server side opens port 5001 or you allow the web client to be used on the external network, the following recommendations can be made for security purposes:
- Password complexity and password protection:
Ensure that the login password for the web client is as complex as possible (at least 10 characters, including digits, upper and lower case letters) to avoid simple passwords being hacked; if the password is leaked for some reason, such as viral infections in the computer, at this time, it may not only be the webclient password leak, other passwords may also leak, so it is necessary for us to do a good job of antivirus work or protection of the computer.
- Restrict the source IP of port 5001 in the firewall or router of 3CX server:
If the public IP of the external web client is fixed, it is better to restrict the source IP of port 5001 in the firewall on the side of 3CX server, so that only specific IP addresses are allowed to login to the webclient, so even if the hacker has cracked the password, he cannot login to the 3CX webclient to make calls;
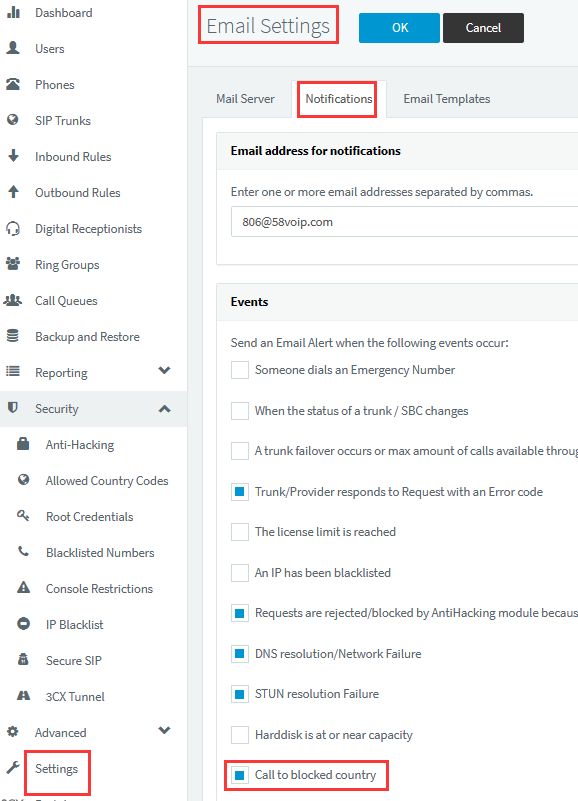
- Restrict the countries or regions allowed to dial:
Administrators can set the countries allowed to dial, so that even if the hacker logs into the webclient to make a stolen call, the cost incurred is limited, and it is best to turn on the email notification for dialing the blocked countries, so that when the hacker dials the numbers from the country that is not allowed, the administrator can receive the email in time to check and deal with the problem of stolen calls:
- Restrict the extension’s access to the management console or the extension’s role:
If the extension has the permission to log into the management console, the user can arbitrarily modify the settings of the management console, such as the countries allowed to call, outbound rules, etc. So at this time, if the hacker breaches the password of the extension’s webclient, the hacker can also use the extension to log into the management console to modify any settings, and the subsequent stolen calls may generate more expensive fees.
Whether the extension can log into the management console is mainly related to these 2 settings:
a. Whether to allow login to the management console and permission settings: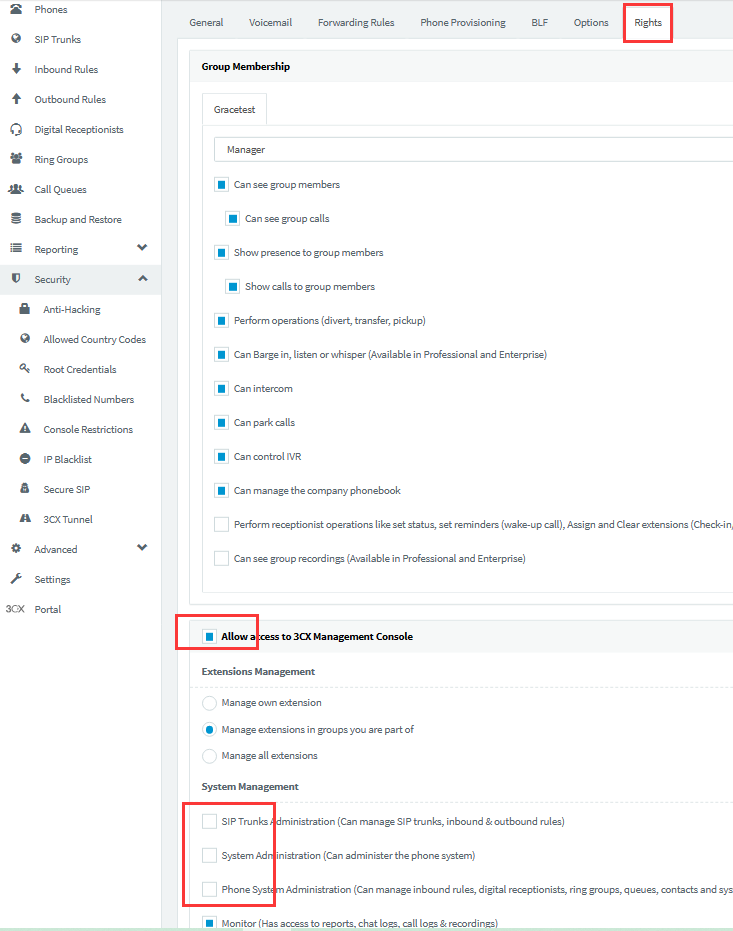
b. Whether the extension’s role in the group is that of a system administrator or system owner: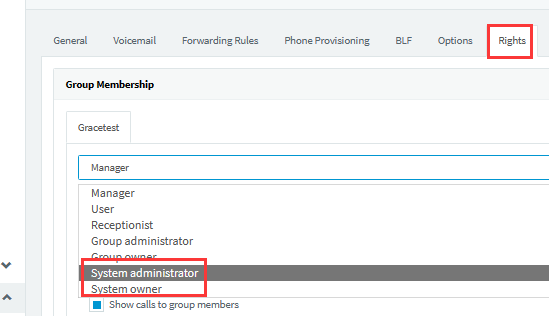
As long as the extension does any 1 of the above settings, the extension can log into the management console. At the same time, the administrator can also set up email notifications so that when the extension logs into the management console, the administrator can also check the problem at the first time:
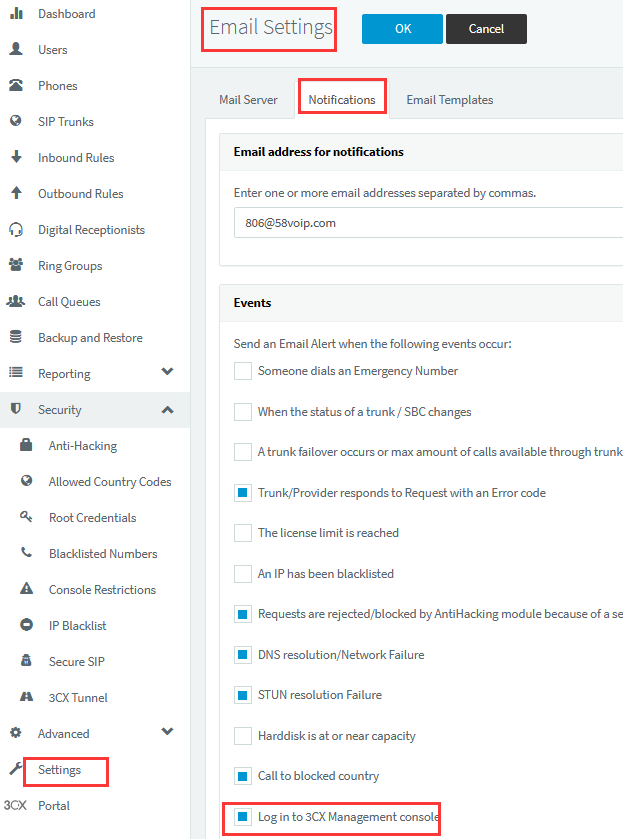
- Set the IP or range allowed to log into the management console:
If the administrator cannot restrict the source IP of 5001 in the firewall and the extension can log into the management console, in order to avoid hackers from using the extension account to log into the management console to modify the settings, the administrator can restrict the IP or network segment allowed to log into the management console as follows: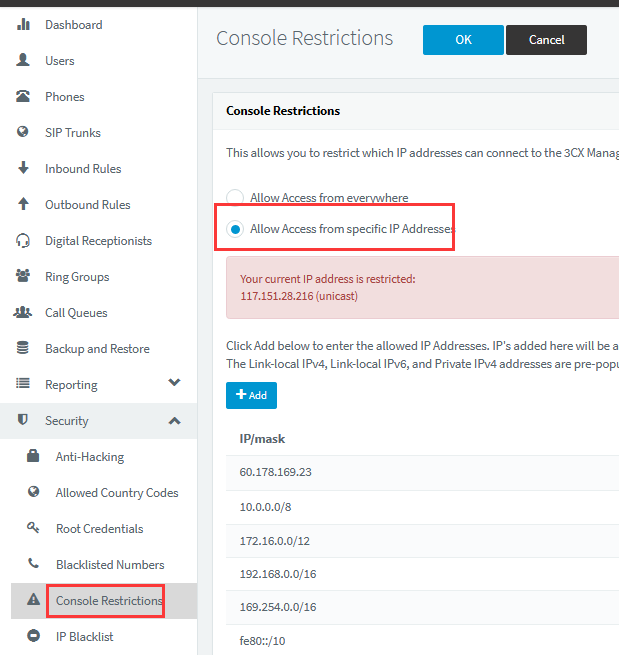
This way only users on a specific IP or network segment can log in to the management console.