We have previously written articles describing how to renew 3CX’s SSL certificate:
- Linux:https://3x.58voip.com/3cx-v15-v16-renewing-ssl-certificate-linux-server/
- Windows:https://3x.58voip.com/3cx-v15-renewing-ssl-certificate/
The certificates used here are for the Nginx server. Usually there are two files, a crt certificate file and a key key file.
In some cases, the certificate provided by the client is in PFX format, which has only one certificate file and also requires a password. This article describes how 3CX can update the PFX SSL certificate.
Install OPENSSL
Since we need to convert the PFX format to a format that 3CX can use, we need to use the OpenSSL software.
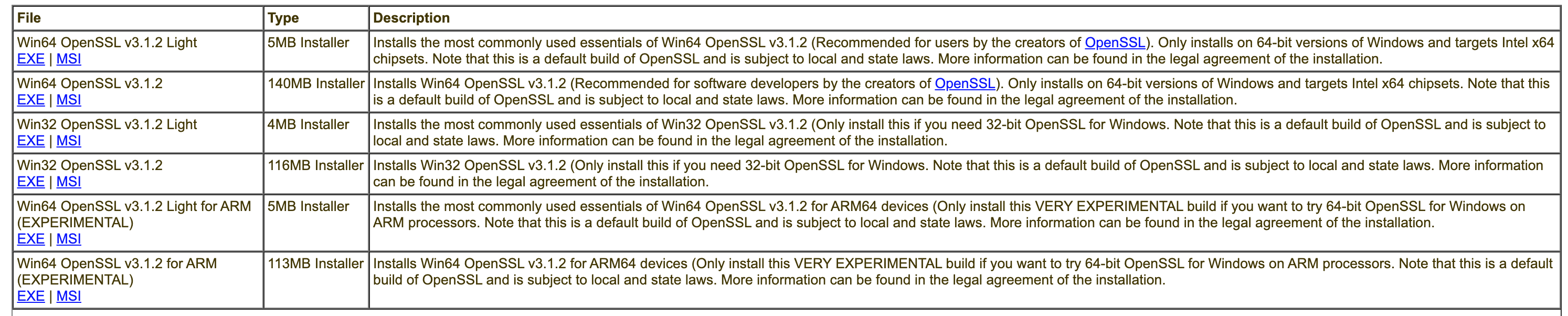
Download openssl here:https://slproweb.com/products/Win32OpenSSL.html
Download it and go all the way to the next step to complete the installation.
After the installation is complete open CMD and enter the following two lines of command:
set OPENSSL_CONF=C:\Program Files\OpenSSL-Win64\bin\openssl.cfg
set Path= C:\Program Files\OpenSSL-Win64\bin
If you change the installation path, you need to change the command above
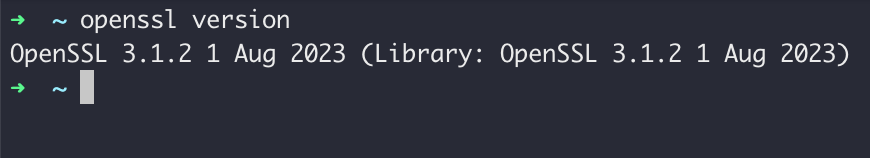
Then we reopen CMD and type openssl version to query the version.
The version is displayed correctly, indicating that the installation was successful!
Convert PFX format
Next, we switch the working path of CMD to the directory where PFX certificates are stored. And execute the following commands in order:
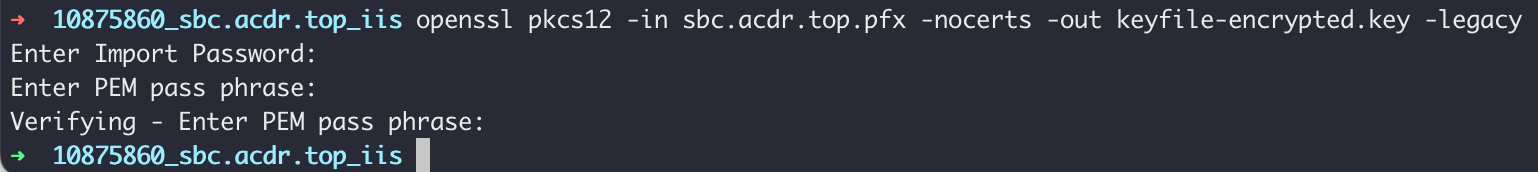
$ openssl pkcs12 -in [证书文件.pfx] -nocerts -out keyfile-encrypted.key
Then you will be asked to enter the password for the PFX certificate. and the PEM pass phrase. just enter the same password for both.
If the above command gives an error, it is because the openssl version is too new and you need to add a -legacy parameter at the end.
$ openssl pkcs12 -in [证书文件.pfx] -nocerts -out keyfile-encrypted.key -legacy
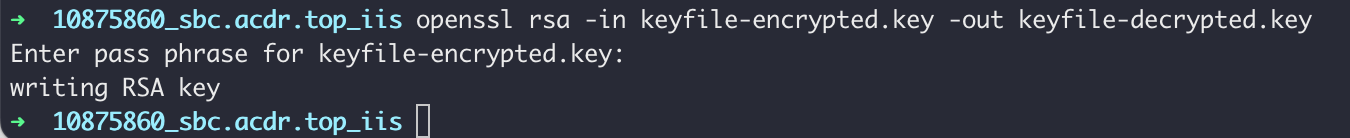
Then enter the following command to decrypt the key file and enter the password:
$ openssl rsa -in keyfil-encrypted.key -out keyfile-decrypted.key
Finally, we’ll generate the certificate file:
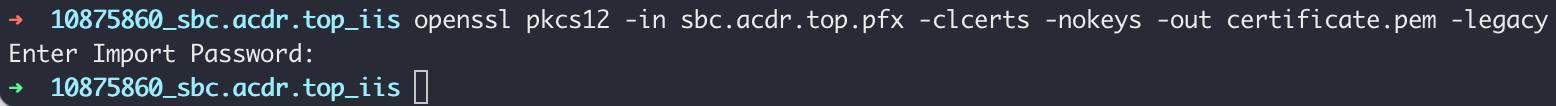
$ openssl pkcs12 -in [证书文件.pfx] -clcerts -nokeys -out certificate.pem
If an error is reported still add the parameter -legacy at the end.
$ openssl pkcs12 -in [证书文件.pfx] -clcerts -nokeys -out certificate.pem -legacy
SSL Renewal
This gives us two files:
- Certificate:certificate.pem
- Key:keyfile-decrypted.key
Next, replace the addresses of the files in the 3CX server with these two files and restart the Nginx service.
- Windows:C:\Program Files\3CX Phone System\Bin\nginx\conf\instance1
- Linux:/var/lib/3cxpbx/Bin/nginx/conf/Instance1
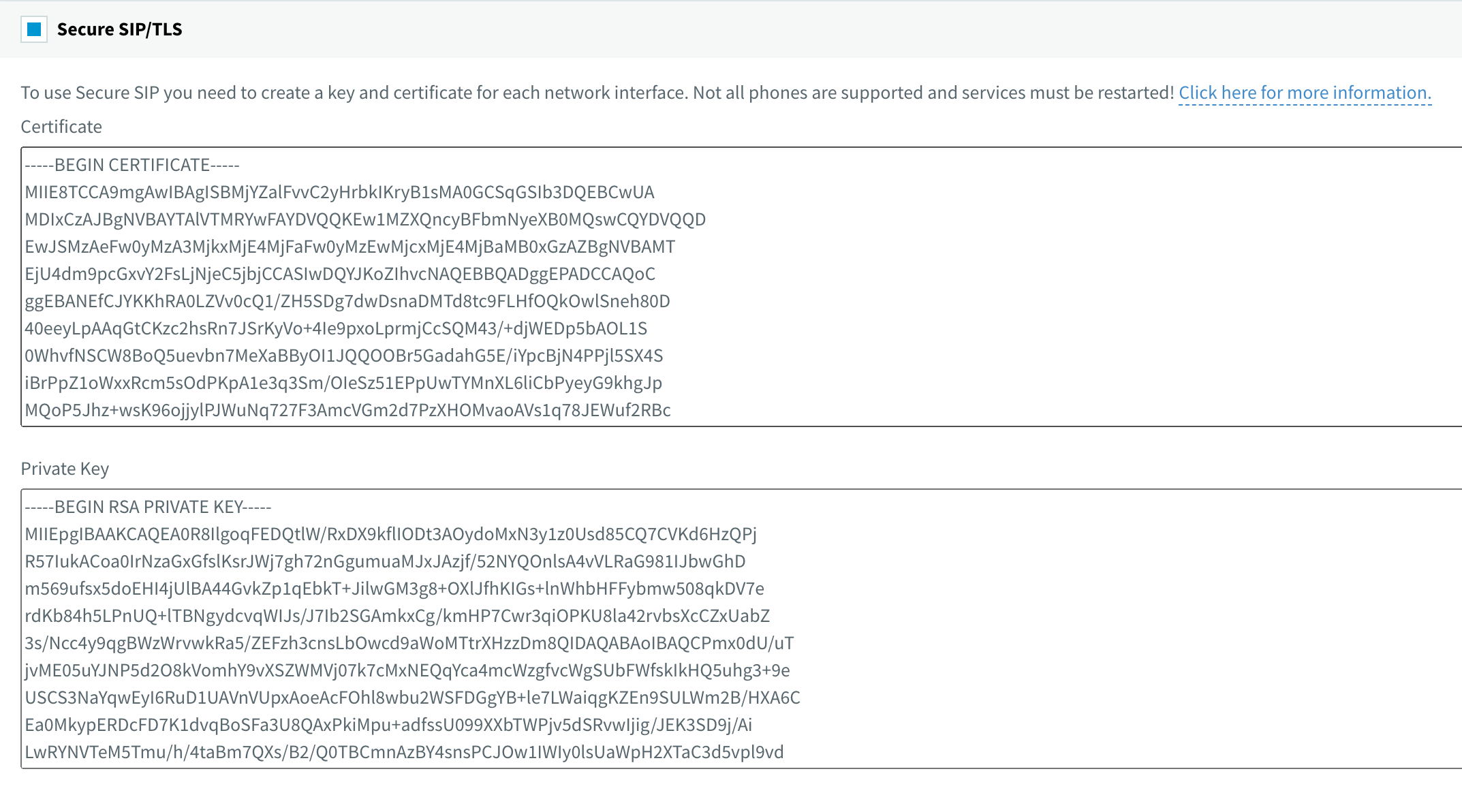
If the phone is registered with TLS, you need to copy the certificate content into the 3CX Management Console -> Security -> Secure SIP.